One of the uprising trends in Red Team vs. Blue Team is the use of the marketing term “Distributed Deception”—offerings which are actually Honey Tokens, Honey Bread Crumbs, and Honey Pots used to detect attackers who have already breached the networks and are developing a plan to compromise or achieve the objective.
However, after reviewing some of the solutions offered by the cybersecurity community, we came to the conclusion that attackers with minimal knowledge can detect some of them or at least try to avoid “Honey-*” that might seem suspicious and/or fake.
Want to know how attackers avoid your deceptions?
Fake Sessions and Injected Memory Credentials Tokens
This LOGON_NETCREDENTIALS_ONLY fake session is a method many solutions use to spread their fake tokens. Attackers can easily detect it when reviewing these two flags:

Mapped Drives and Credentials Manager Breadcrumbs
Another method used by more deception solutions is to spread their tokens via the Credentials Manager. The detection here might be trickier, but it is still possible. Correlating with more data collected from the Active Directory about the fake user token and target server, attackers realize they’re probably fake.

Is your vendor telling you their solution is “not a honey pot/token/breadcrumb/etc” ? Test it and find out with the Honeypot Buster tool.
During the research, we revealed there are 7 common types of Active Directory related Honey Tokens you might encounter as a Red Teamer:
1. Kerberoasting Service Accounts Honey Tokens, just like the one described in this ADSecurity article by Sean Metcalf.
Tricking attackers to scan for Domain Users with assigned SPN (Service Principal Name), and with {adminCount = 1} LDAP Attribute flag.
So when you try to request TGS for that user, you’ll be exposed as Kerberoasting attempt.
TGS definition: A ticket granting server (TGS) is a logical key distribution center (KDC) component that is used by the Kerberos protocol as a trusted third party.
2. Fake Memory Credentials Honey Tokens, creating a process using the ‘NetOnly’ flag will result a “cached fake login token”. Once the attacker tries to steal and use these credentials – he’ll be exposed.
This method is used by the DCEPTproject, Invoke-HoneyHash and other Deception companies.
3. Fake Computer Accounts Honey Pots, creating many domain computer objects with no actual devices associated to them will result in confusion to any attacker trying to study the network. Any attempt to perform lateral movement into these fake objects will lead to exposure of the attacker.
4. Fake Credentials Manager Credentials Breadcrumbs, many deception vendors are injecting fake credentials into the “Credentials Manager”, these credentials will also be revealed using tools such as Mimikatz. Attacker’s might confuse them as authentic credentials and use them although they aren’t real.
5. Fake Domain Admins Accounts Honey Tokens, creating several domain admins who have never been active and their credentials should never be used. Luring attackers to try brute-forcing their credentials. Once someone tries to authenticate to this user, alarm will be triggered and the attacker will be revealed. This method is used by Microsoft ATA.
6. Fake Mapped Drives Breadcrumbs, many malicious automated scripts and worms are spreading via SMB Shares, especially if they’re mapped as Network Drive Share. This tool will try to correlate some of the data collected before to identify any mapped drive related to specific Honey Pot server.
7. DNS Records Manipulation Honeypots, one of the methods used by deception vendors to detect usage of fake endpoints, is registering their DNS records towards the Honeypot Server. They will be able to point the attacker directly to their honey pot instead of actual endpoints.
The main idea behind these Honey Tokens is to lure attackers to use them, letting them think they’re on the right path to achieve privileged credentials or spread through the domain environment. However, attackers can study these Honey Tokens/lures and easily avoid them.
Using simple validations that take only a few minutes, an attacker can identify objects that are fake and avoid the trap. The validation of attackers and avoidance of Honey Tokens can be done without triggering any alarm and without authentication or lateral movement.
These results can be integrated with Red Team tools such as Empire or Bloodhound to enhance the automation of Red Team hacking processes.
Introducing Honeypot Buster
A unique tool that allows any Red Teamer to identify and avoid traps. The tool detects all seven common types of Active Directory related Honey Tokens you might encounter as a Red Teamer or adversary.
Written in PowerShell, it supports version 2.0 and above and has remote WinRM capabilities for the 2nd and 4th Tokens gathering. It leverages LDAP Queries to find domain objects and loads DLL to access the LSASS process for local tokens gathering (might trigger AVs soon). Honeypot Buster supports all Windows OSs; however, some of the features will not work with Windows Credentials Guard and Windows 10 Creators Update.
https://github.com/JavelinNetworks/HoneypotBuster
Invoke-HoneypotBuster
-CsvOutput “export folder path”
Export the results to csv files.
-ComputerName “hostname”
Remote endpoint to run the FakeCredMan and FakeSession gathering on, accesses LSASS, using WinRM.
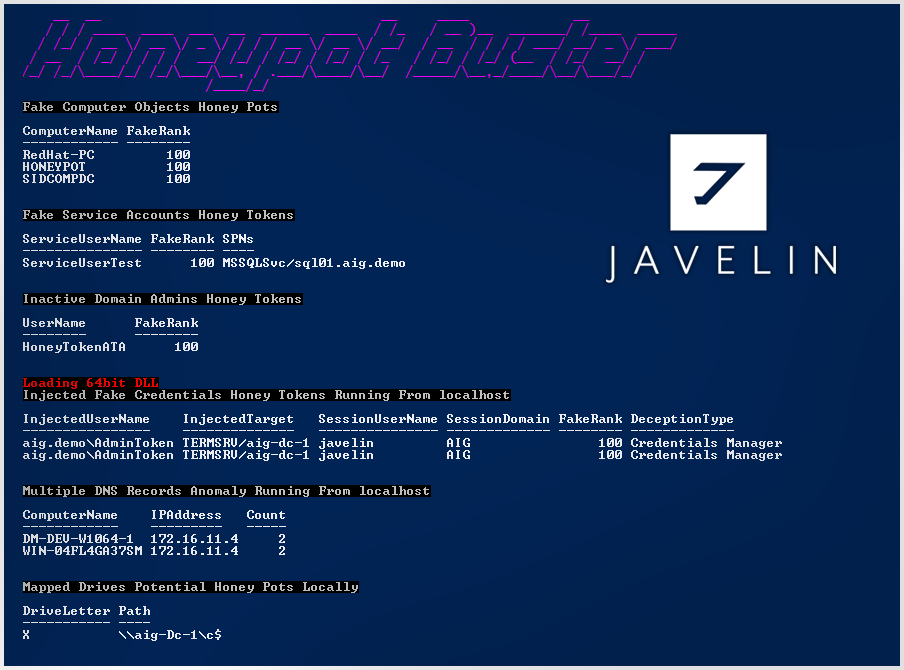
https://github.com/JavelinNetworks/HoneypotBuster
Just import the module and execute the function:
Import-Module .\Invoke-HoneypotBuster.ps1
Invoke-HoneypotBuster
Give it a try!
Contact us: [email protected]


Comments